Why Is It Slow?
When you request a website, say, b3n.org, your computer needs the IP address. So it sends out packets through your router/firewall, your modem, and out to your ISPs DNS Servers. Your ISP’s DNS server will probably have it cached, if not it queries the authoritative (starting with the Root Name Servers) recursively to find out what the authoritative DNS servers are and then queries those DNS servers. It gets the IP address, and sends it back to your computer. Your computer can then query the server IP for b3n.org. Any latency along this process will result in delays. If you ever type in a url in the address bar and nothing happens for a few hundred milliseconds and then suddenly the website starts to load this is likely the problem.
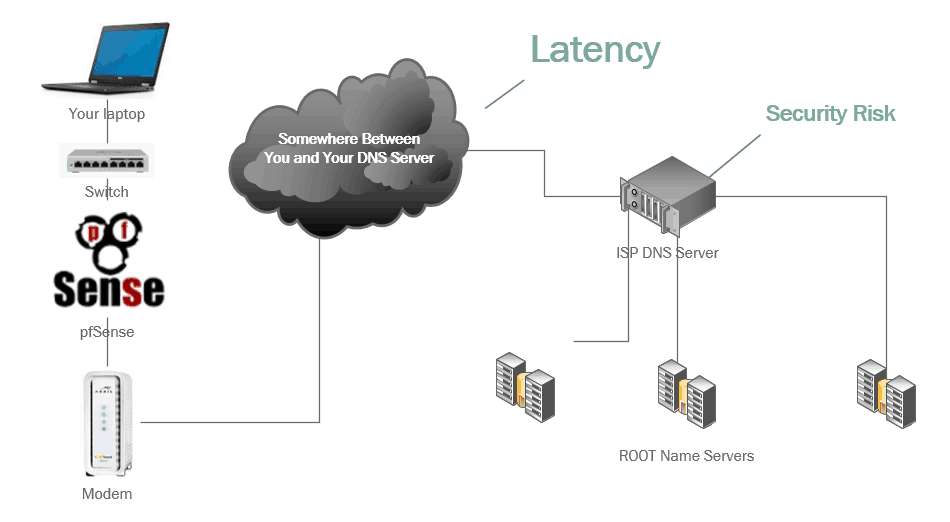
Is Your DNS Hijacked by Your ISP?
It’s pretty easy for ISPs to hijack DNS queries. A small number of ISPs (Comcast, CenturyLink, Time Warner, Cox, Rogers, Charter, Verizon, Sprint, T-Mobile, Frontier, etc.) have been caught doing exactly that. Want to know why? Advertising revenue. When you misspell a domain some ISPs, instead of returning an NXDOMAIN (does not exist) like any RFC compliant DNS server it will resolve the domain anyway, point it at a page they control, and advertise to you! This is a really bad idea. But there is a way to prevent your ISP from doing this…
Using Google’s Nameservers
If you’re not tech savvy using 8.8.8.8 and 8.8.4.4 is probably better than your ISPs nameservers. It won’t hurt, and will probably help, but it may not help… it’s very trivial for an ISP to route those IPs to their own servers and some do.
Even if your ISP is pure goodness and would never do that, someone could setup a rogue DNS server posing as theirs and intercept all your DNS traffic.
The only solution is to query the Root name servers for authoritative DNS servers and use DNSSEC. Cut out any 3rd party DNS provider and run your own DNS server locally.
Setup an Unbound Server on pfSense
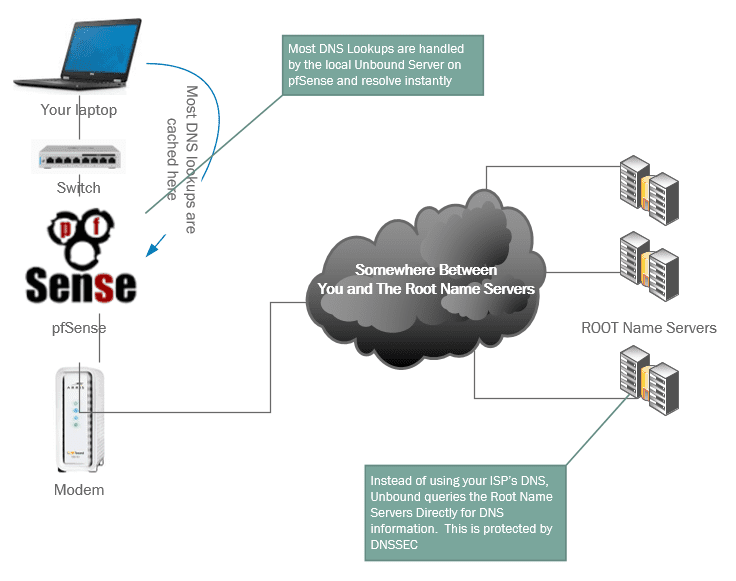
Unbound is a high performance caching DNS server. Unbound queries recursively authoritative DNS servers directly, completely bypassing your ISP. It uses DNSSEC to make sure your queries haven’t been tampered with. And best of all, it caches DNS results locally (like your ISP would) but since it’s on your own network, the cached DNS queries are local!
You can setup a local FreeBSD server and run Unbound on it, but if you’re already using a router like pfSense or OPNsense you can setup an Unbound server in a few clicks.
Open up pfSense, first make sure the forwarder under Services, DNS Forwarder, is disabled. Slowness warning: if you are running a low query lookup network such as on your home network having the forwarder disabled may cause lookups to be slower because you’re having to traverse the DNS servers regularly to get results… this can sometimes take a second or two and result in DNS timeouts while it’s trying to traverse the DNS nameservers. If you find that unbound performance is slow I’d suggest turning on forwarding mode which will use the DNS servers specified in pfSense under system, general setup. In this case I’d recommend pointing them at 8.8.8.8 and 8.8.4.4. If you run with forwarding enabled you should verify that your ISP is not hijacking your DNS results, if they are you should switch ISPs.
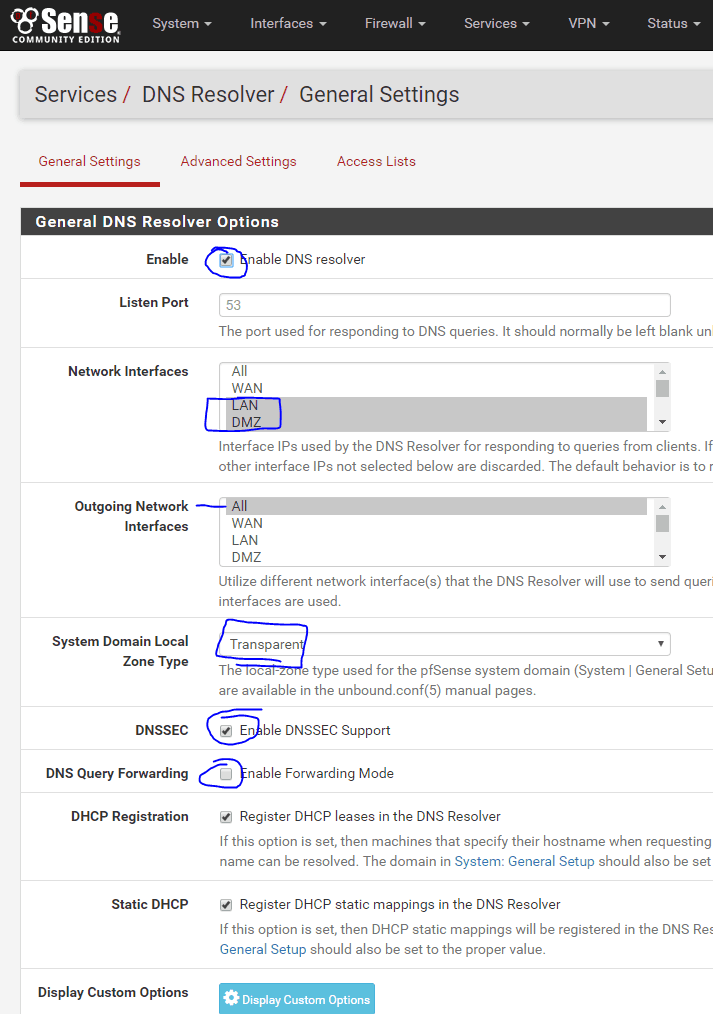
- Go to Services, DNS Resolver.
- Enable the DNS Resolver
- Select the Network interfaces that you want Unbound to listen on (do not select ALL, you’ll definitly want to select LAN).
- System Domain Local Zone Type: Transparent
- Enable DNSSEC Support
- Do NOT enable Forwarding Mode
- You can also choose to register DHCP addresses in the DNS Resolver which is very handy if you’re using pfSense to manage DHCP.
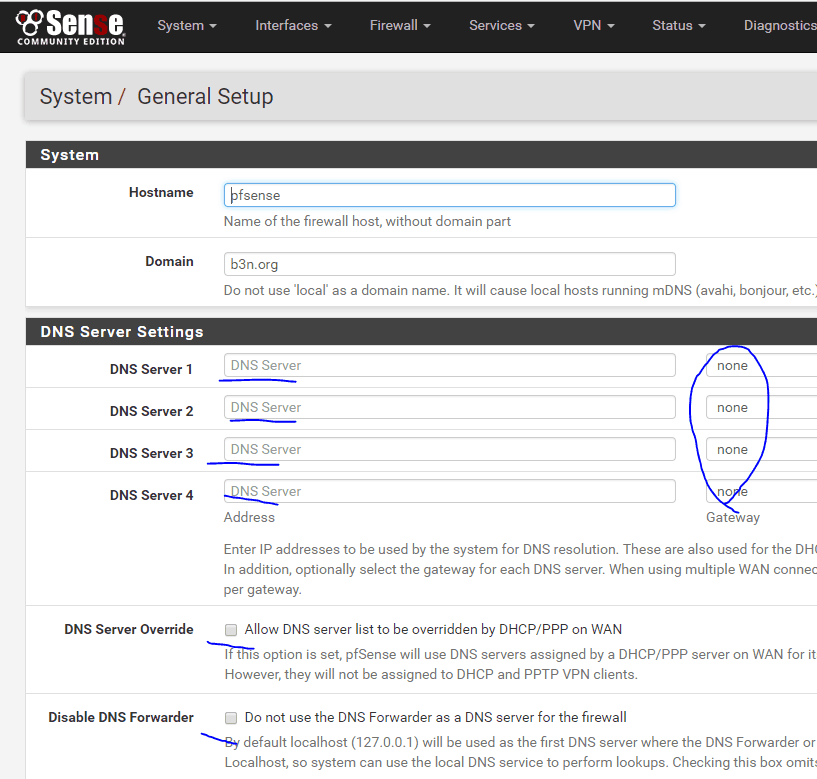
- Under System, General Setup
- Make sure all DNS Server fields are empty. DNS Server Override and
- Disable DNS Forwarder should be unchecked.
Finally, Under Services, DHCP Server, set your DNS Server to your pfSense’s LAN IP. As your DHCP clients renew their lease they’ll start using pfSense for DNS.
As far as performance if you have low latency to your ISPs DNS you probably won’t notice anything. But if you’re on a high latency connection with 70ms pings like I am, this makes a big difference.
Thanks for your blog! Helped me successfully virtualize FreeNAS last year on ESXI 6.0. With regard to running Unbound on PFSense in a home solution, if you are using certain hosts configured with an openvpn client, how does unbound complicate the first DNS lookup sent by the host when trying to initially connect to the VPN url? Is it better to make sure all queries go through Ubound with DNSSEC enabled or forcing those clients to use the vpn’s DNS Servers?
Also, specific to the above, why disable the forwarder and then ensure this under DHCP server settings? “Disable DNS Forwarder should be unchecked.”
You’re welcome. I don’t think unbound would make a difference with the VPN… the potential downside is the DNS lookup will be slower and possibly fail, and the potential upside is your DNS won’t get hijacked. Once you connect to the VPN, depending on the VPN configuration you may still be using your local pfSense DNS server, or the VPN may provide it’s own DNS server in which case your queries will hit that instead of pfSense.
When you disable the forwarder you’re telling pfSense to traverse the authoritative DNS servers directly, if it’s enabled you’re telling pfSense to query whatever nameservers you have specified. Either way, you want to tell DHCP to point your clients DNS at your pfSense server.
Thanks a lot. Helped me to learn more about my pfSense.
It works and seems to be faster, but
if I put under Services>DNS Resolver>General Settings>Network Interfaces “LAN” only (I have only one LAN) as per yr advice pfSense says when saving:
“The following input errors were detected: This system is configured to use the DNS Resolver as its DNS server, so Localhost or All must be selected in Network Interfaces.”
Also there is a remark: “Interface IPs used by the DNS Resolver for responding to queries from clients. If an interface has both IPv4 and IPv6 IPs, both are used. Queries to other interface IPs not selected below are discarded. The default behavior is to respond to queries on every available IPv4 and IPv6 address.
Putting “All” there is accepted!
Does DNSSEC Support work out of the box with pfSense? Doesn’t it need (installation/registration of) certificates or something similar?
I have MultiWAN with 2 interfaces (VDSL and LTE) with 2 Gateways and a gateway group with load balancing in pfSense.
System>General Setup>DNS Server Settings>DNS Servers is now empty. No DNS servers in general setup anymore!
https://doc.pfsense.org/index.php/Multi-WAN#DNS_Considerations says there should/must be a least one DNS server per WAN port/interface.
What about this now? Does it matter?
Regds
AW
Thank you for your help! My website under construction was redirected somehow to sedoparking.com. When I talked to Sedo, the tech pulled up my website and saw my content. I looked at it on my phone, and it was still going to sedo. Turned off the wifi, and viola, there was my website.
I followed your instructions (except Pfsense requires ALL, not LAN) and now my website is there. I guess my ISP hijacked it or maybe I was hacked somewhere. Not sure which, I just know that now I can get back to work on my site. Thank you so much!!!