What is DNS Content Filtering?
A DNS Based Content Filtering service can prevent certain websites from loading on your network. Most services can filter by specific categories like malware, phishing, pornography, etc. Unlike some content filtering that can introduce security risks, DNS filtering does not intercept traffic between you and the website you’re visiting. It doesn’t require installing any software on your computer or device, making it one of the safest ways to filter web content.

If you accidentally typo a popular domain (such as typing “.cm” instead of “.com”) it would normally take you to a phishing site. A DNS filtering service would block your computer by returning NXDOMAIN (domain does not exist) instead of the IP address blocking the website from loading. The same technique can prevent any undesirable categories such as malware, pornography, and adware from loading on your network.
The other benefit of using a DNS filtering service is it can force certain search and media services (like Google and YouTube) into safe mode preventing anyone using your network from even seeing adult content in their search results.
Why Should You Use DNS Filtering?
It’s not only a wise way to protect yourself from malware and temptation but also when letting guests on your WiFi network—you don’t have to worry (as much) about what they’re doing, and also a good idea when you let kids online. DNS filtering doesn’t take the place of parenting, and anyone with a little technical skill can bypass it, but it may help prevent your family and anyone on your network from accidentally stumbling across bad sites. If it prevents one malware infection, it’s worth it.
Families, churches, home labs, small businesses, organizations, schools, large enterprises, and governments should use DNS filtering. You may not want to go overboard blocking research content about illegal drugs and gambling, but at the very least you don’t want malware on your network!
Three DNS Filtering Services
There are three free DNS Content Filtering services I recommend. I use OpenDNS, but I’ll go over all three so you can make an educated choice about what works best for you. All have simple instructions to get started so I won’t repeat that here. All are free, work well, and my decision to use or recommend one or the other depends on the situation—although in most cases any would be better than nothing! It’s nice to have multiple good choices.
OpenDNS

OpenDNS has been around since 2006 and was acquired by Cisco in 2014. It offers several free plans, and some paid options as well:
- OpenDNS Family Shield (Free). Very simple—just set your router’s DNS servers to 208.67.222.123 and 208.67.220.123 and it is pre-configured to block malicious and adult content.
- OpenDNS Home (Free). For more advanced control. This is what I use. This requires some skill to set up so if you’re not technical, skip this option. The reason I like this option best is OpenDNS Home allows for granular category filtering as seen in the screenshots below. If your ISP has a dynamic IP, you will need to use a DDNS client to update OpenDNS with your public IP. Below are some screenshots to show the options and categories:
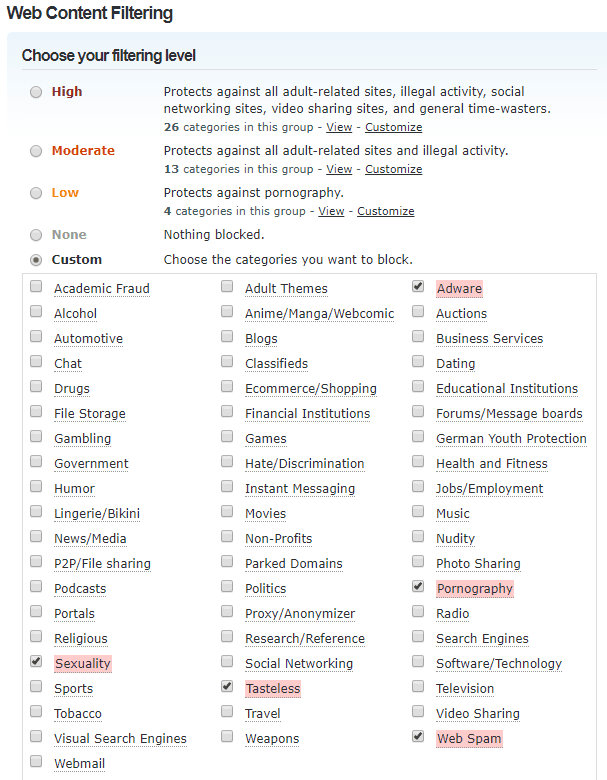
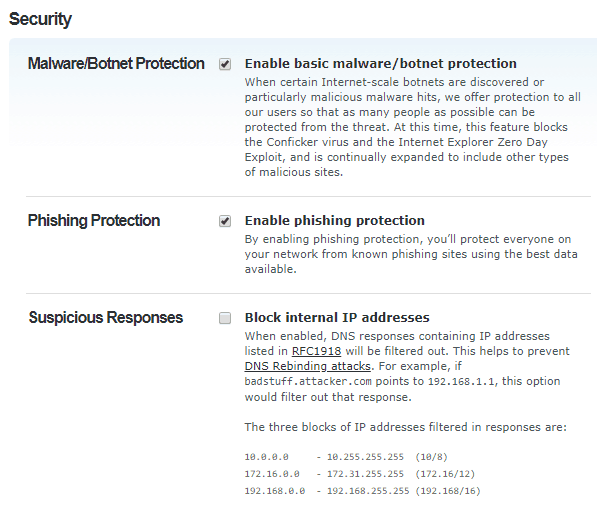
- OpenDNS Home VIP ($20/year) — Very affordable and adds the ability to white-list specific domains if they’re on the block list.
- Cisco Umbrella — For businesses and larger enterprises.
CleanBrowsing
CleanBrowsing is a fairly new service, starting in February 2017.
It offers three easy free filtering plans and 2 paid plains:
- Security Filter (Free) – Set your router’s DNS to 185.228.168.9 and 185.228.169.9 to only block malicious domains (phishing and malware).
- Adult Filter (Free)– Set DNS to 185.228.168.10 and 185.228.169.11 to block Adult domains, set search engines to safe mode (also includes the security filter).
- Family Filter (Free)– Set DNS to 185.228.168.168 and 185.228.169.168 to block access to VPN domains that could bypass filters, mixed content sites (like Reddit), and sets YouTube to safe mode (includes Adult and Security filters as well).
- Basic Plan for Home ($55/year) allows you to set up custom filtering categories and whitelist and b5lacklist specific domains.
- There are several plans ranging from 100 to 2000 devices and you can get a quote if you need more than that.
1.1.1.1 For Families
Cloudflare just launched a new service, 1.1.1.1 for Families on April 1, 2020.
Cloudflare has been providing unfiltered DNS on 1.1.1.1 since 2018. And is undisputedly the fastest DNS service in the world according to DNSPerf.
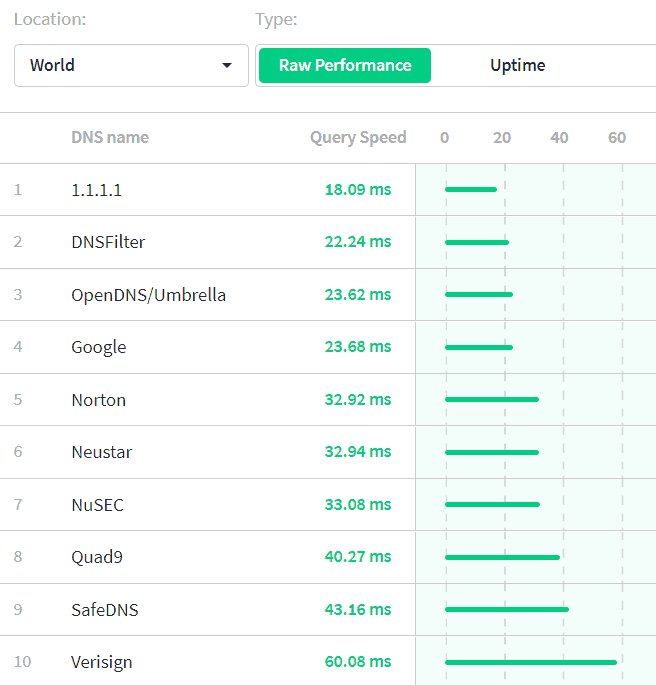
1.1.1.1 for Families offers two options:
- Block Malware only (Free) — Set DNS to 1.1.1.2 and 1.0.0.2
- Block Adult Content & Malware (Free) — Set DNS to 1.1.1.3 and 1.0.0.3
There are no custom options, not even a paid plan. But what you will get from Cloudflare is an impressive number of data center locations providing low latency anywhere in the world.
OpenDNS, CleanBrowsing, and 1.1.1.1 for Families Comparison
OpenDNS is the most configurable on a free plan. CleanBrowsing is further ahead in supporting security features and is faster at blocking harmful sites. 1.1.1.1 for Families will have the lowest latency and is the newest major competitor in this space.
OpenDNS advantages
- The free account has the best control with the ability to block specific categories
- Blocked domains get redirected to a page saying why the page is blocked (this results in the user understanding of what’s going on than an NXDOMAIN for most people)
- Been Around Longer. More mature.
CleanBrowsing advantages
- Security – Supports DNSSEC (prevents forgery of DNS results …some ISPs have hijacked DNS results). It also supports DNSCrypt, DNS over HTTPS, and DNS over TLS.
- Blocked domains return an NXDOMAIN (better practice than redirecting for technical/security folks)
- Privacy Policy: CleanBrowsing States it does not log requests
- Better Test Results on Adult content filtering: blocked 100% of adult content on a Porn Filter test by Nykolas Z (OpenDNS blocked 89%).
- Much better Test Results Blocking Phishing Sites: CleanBrowsing blocked 100% of phishing sites on 3 out of 4 tests beating out OpenDNS in every area. On the real-time test it allowed 1 out of 12 sites through, however, OpenDNS only blocked 2 out of 12 sites.
1.1.1.1 For Families
The newest service from Cloudflare is promising. It blocks malware and adult content. With Cloudflare’s experience, it will be the fastest and have strong privacy guarantees. Cloudflare is security-minded supporting DNS over HTTPS, DNSSEC, and DNS over TLS.
Helpful?
I hope this post has been helpful. OpenDNS, CleanBrowsing, and 1.1.1.1 for Families have quick DNS resolution times (probably faster than your ISP). I’ve used all three, but currently, I’m using 1.1.1.3 and 1.0.0.3 for my house. Decide which one works best for you and use it.
…
I have made a covenant with my eyes.
How then could I look at a young woman? — Job 31:1 CSB
There really isn’t any such thing as “DNS Content Filtering”. When using DNS specifically to decide which sites are accessible and which are not, you are performing DOMAIN filtering. While certain domains do typically correlate to certain kinds of content, that is not necessarily the case.
In today’s world of virtual hosting where multiple web sites (multiple domains) can land you on the same exact box with access to the same exact back-end content, using DNS to filter out domains isn’t anywhere near enough.
Additionally, DNS has no concept at all of the actual content, including whether or not there is something potentially malicious that has become inserted into otherwise safe content. In order to properly, FULLY protect yourself, you need a true content filtering product. Period.
Thanks Mark. That’s a really good distinction to make. Agreed, the content filtering isn’t going to be real-time. It also can’t be precise for mixed content sites (we either have to block them or allow them unless they provide alternative IPs for safe content). And like you said it does rely on trusting domains to not get hacked and host the same kind of content they historically host. The way I look at it is DNS filtering is a low effort low cost way to add a layer of protection with huge benefits. We can always add more layers of filtering. It’s also low risk. We don’t have to implicitly trust a DNS provider because if they returned wrong IPs we should notice DNSSEC validation failures not to mention SSL certs failing as well.
Correct me if I’m wrong, but my concern with content filtering systems that examine content over the wire in real-time is that I can’t think of a way to do that for https other than SSL inspection–which means we have to implicitly trust (e.g. trust with our passwords, etc.) it with all information we send and receive. Not only do you have to trust the integrity of vendors and admins of the system but you have to trust them to be competent and vigilant enough for it not to get compromised. There are valid use cases for content-filtering, but for people who don’t have a robust security team I think it introduces more potential for risk than for benefit.
While you’re right that a content filtering system would be able to see EVERYTHING you send, including passwords, that doesn’t mean that you have to filter those sort of sites.
Just like with DNS filtering you are able to implicitly trust certain domains / sites, you can configure inspection policies for content in a similar manner. Whitelist your banking site and the content filter will ignore that site and not try to filter content – essentially the exact same thing you get with DNS filtering only.
If you are relying on a machine that is out of your control to do the filtering (you set yourself up to use an external, third-party, proxy-based solution), then you may have some significant cause for concern. If the software runs entirely locally on your machine, that concern is reduced so long as the software comes from a reputable company that has no potential to “phone home” after capturing your credentials. And, those systems run in memory without committing inspected content to disk. So, another rogue program on your machine wouldn’t have a way to snoop that information either.
Nice article Benjamin. CleanBrowsing while not specifically mentioned on their website, offers DNS servers that will return a block page for those that prefer that method. For example the adult name servers with the block page are: 185.228.168.11 & 185.228.169.11
I didn’t know that, Thanks Joseph!
Thanks Joseph. I confirmed that those addresses do redirect to a block page. It’s interesting that these aren’t mentioned on their website (or anywhere else that I could find). The 2nd one surprised me because it’s listed as the “normal” secondary DNS for the adult filter:
https://cleanbrowsing.org/filters
Guys, could I ask if it is possible that using Clean Browsing could lead to the hacking of information or accessing of my ISP services? Is it secure, routing all of your information through their servers?
It’s not.
That would be equivalent to transcripts of your phone calls being sent through the phone book (DNS is the “phone book” of the Internet).
Hi Mark,
I’m curious to understand further about your comments on domain and content filtering. If the recommendation is to couple domain and content filtering, what are the options for homes and small business?
Content filtering for the home user is “hard” because it typically requires either a reasonable amount of technical know-how, money, or both. I used to use a blocklist tool that plugged into Squid (called SquidGuard). It required policy routing and/or iptables configurations on the box that held the squid proxy or you had to forcibly configure your web browsers to use it as a proxy. With so much moving to encrypted connection, and limitations on the SSLBUMP option, I ultimately opted to back away from that setup and just learn to be smarter about where anyone browsed along with good anti-malware software.
For small business, it’s less about the technical know-how and more about how much of a ransom you’re willing to pay to your Internet provider every month to add this sort of thing on. It isn’t until you get to the medium-sized business and above where your options actually get useful (meaning you have enough technical staff AND enough money in your budget to do something meaningful that works).
I’m a mom of 3, thank you or this info was very helpful, God bless.
Glad to hear! Thanks.
Hi thanks for this article.
I am the developer of DNS For Family: https://dnsforfamily.com and it’s motive is just to block porn websites and advertisements (as some ads leads to porns). Database is updated daily at fixed time.
Secondly, unlike other services you listed. DNSforFamily there is no profit motive and it is designed completely for humanitarian approach.
By any chance you could enter this service in your article so that readers can know about DNSforFamily also.
Thanks Again.
Can you use more than one of these 3 services at the same time? any drawbacks? Thanks for the helpful review.
Hi, Howard. I can’t think of a way to use more than one service at a time. You can only point your DNS at one of them.
Nice article for decision making on DNS filters. Thank you!
Personally, I can’t recommend OpenDNS since it’s now a part of Cisco, and Cisco is a Great Firewall provider for China. So I don’t think Cisco would be a company that respects humanity when it has a chance to make money.
For more information about the Great Firewall of China, please read https://en.wikipedia.org/wiki/Great_Firewall
Thanks for pointing that out, Someone. I didn’t realize Cisco was involved in the Great Firewall of China. It’s ironic that China needed the help of U.S. companies to implement their firewall and disappointing that they would be willing to participate in that for profit. What a moral failure.
It’s quite a stretch to say that Cisco is making money instead of respecting humanity as much as it is to say that they are a Great Firewall “provider.” The Chinese Government is 100% responsible for the policies of the firewall, not Cisco or any other technology company.
The firewall would be exactly the same if it were controlled by Checkpoint, Palo Alto, or any number of a dozen other firewall products on the market.
Mark, shouldn’t tech companies bear responsibility for how tech is used when it’s in their power to do so? Why would you think Cisco bears no responsibility here? I agree that the Chinese Government is responsible and it could be built on any vendor’s equipment. But I don’t agree that Cisco doesn’t bear some responsibility if they’re supplying equipment knowing that it’s used to suppress their own citizen’s rights. Now if the Chinese government bought the equipment without telling Cisco what it was intended for, that’s an entirely different matter. But that doesn’t seem to be the case. I don’t see a statement from Cisco condemning China’s use of their equipment which is what I should expect. In fact, I see this: https://www.eff.org/deeplinks/2016/04/ciscos-latest-attempt-dodge-responsibility-facilitating-human-rights-abuses-export which indicates Cisco is more concerned about making a profit in any way legally possible than doing what is right. Sure, China could go to another vendor, but if all of the vendors refuse to help China it would be a lot more difficult for them.
It’s companies without a moral compass like Cisco that necessitate the need for new U.S. laws that shouldn’t need to exist. The fact the legislature is even having to talk about introducing a law against this is an ethical failure.
An analogy would be if Kim Jong-Un asked Ruger to supply firearms that he would use to kill his own people. Sure, Kim Jong Un could get the weapons from Glock, S&W, etc. But doesn’t Ruger have some obligation to refuse to take part in this?
I believe that we can have great conversations about technology as we have actual, direct knowledge of it based on verifiable facts. We can all reproduce the sort of details that are written about by spinning up environments in our own homes.
Beyond that, it gets very muddy very quickly and the ability to relate back to actual, verifiable facts goes away pretty quickly.
Could the same argument about gun companies in the USA? Guns are used in most crimes. But gun companies are not responsible. Can you really say that the great firewall is responsible for as many deaths?
Good questions, Alex. There is a difference in intent. Gun companies would be in the wrong if they knowingly sold guns to criminals. But Cisco knew who they were selling to and how it would be used. Despite that knowledge they proceeded anyway.
Mark, could you expand on why you chose OpenDNS free over the other offerings? I’m interested in CleanBrowsing since it does a better job filtering content. So why have you stuck with OpenDNS?
Mark, I really apprecaite this article. However, I see that it is about 5 years old and that Eric’s 2021 question went unanswered so I’m not sure if you’ll see this but I am wondering similarly wondering if you’re still using 1.1.1.1. If so, why? That service seems to have the least information and features (other than speed which isn’t unimportant) so I’m curious if you’re still with it and/or if your recommendations are the same 5 years later. Thank you!
Hi, Ryan! I’m still using 1.1.1.3 and it’s working fine and has never gone down so I honestly haven’t re-evaluated or looked to see if there is new research or if someone has done a newer comparison in the last 5-years. Like you said Cloudflare is typically top on performance, and OpenDNS gives you fine-tuned options to filter exactly what you want. I have found a few cases where CleanBrowsing blocked some sites I was trying to visit (this was awhile go so may not be an issue now) so it may be a bit overzealous but if you’re primary purpose is to have it on your home network that may not be a bad thing.
Another thing I have found is innapropriate ad content on websites, and especially in YouTube ads. The Brave browser seems to work best. I also use the paid 1Blocker extension with Safari but it doesn’t filter quite as well as Brave.
Apologies, that meant to be addressed to Benjamin, the original author. I missed that Eric’s comment was directed to another commenter.