*** DEPRECATED StartCom no longer exists. Please see my newer SSL Certificate Guide Using Let’s Encrypt ***
Here’s a quick tutorial on how to obtain and setup a certificate from StartCom.
StartCom offers free personal certificates, these aren’t the fake certs where you have to setup your own CA and it only works when people have your CA cert installed. These are real certs that work out of the box in just about every OS / browser I’ve tried (OSX, XP SP3 to Windows 8, IE, Firefox, Safari, Chrome, iOS, Android, Windows 8 Phone, etc.).
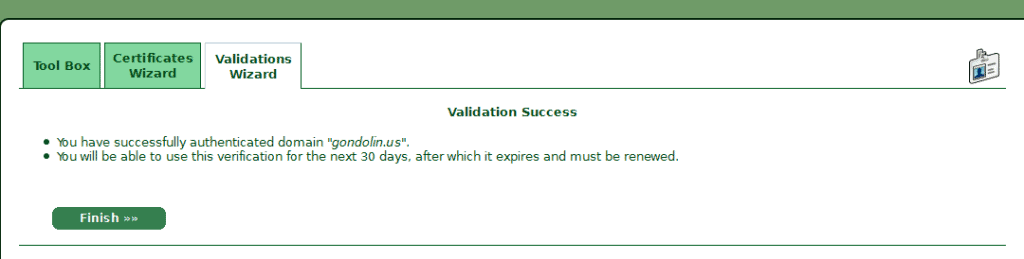
Validate Your Ownership of the Domain
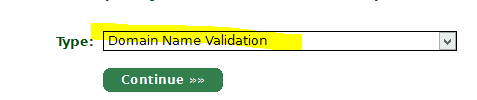
1. Select Domain Name Validation
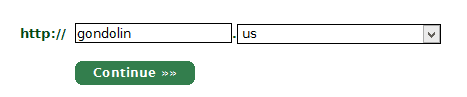
2. Enter the domain name you want to validate.
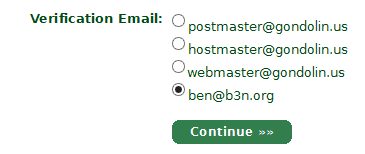
3. Select an address you can receive email at, the final address comes from your whois record which should be the domain owner’s email address. StartCom will send you a validation code, once entered you have verified domain ownership and can create certificates for 30 days.
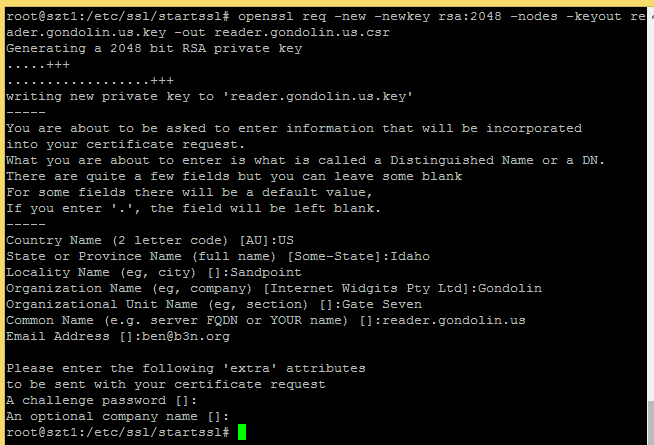
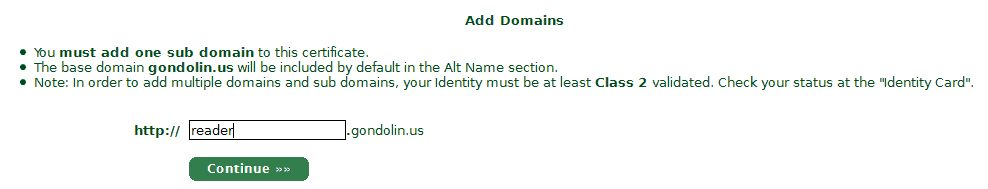
4. Generate Certificate Request. SSH into your server and create a new key and CSR, it is of extreme importance that “Common Name” should be your fully qualified domain name. StartCom won’t let you enter a naked domain (e.g. b3n.org) here, you must enter a sub-domain (such as www.b3n.org) or in the example below I used reader. The cert will also be good for your naked domain.
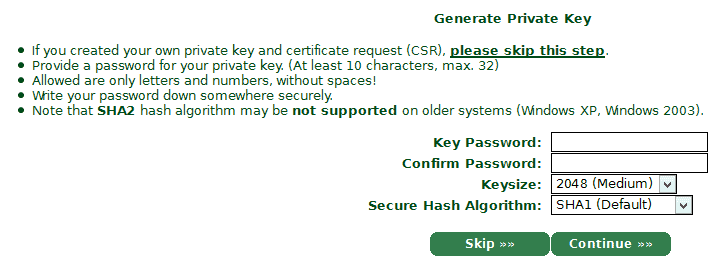
Skip the generate cert option (since you’ve already generated it) and paste the contents of the CSR file you create into the certificate request form.
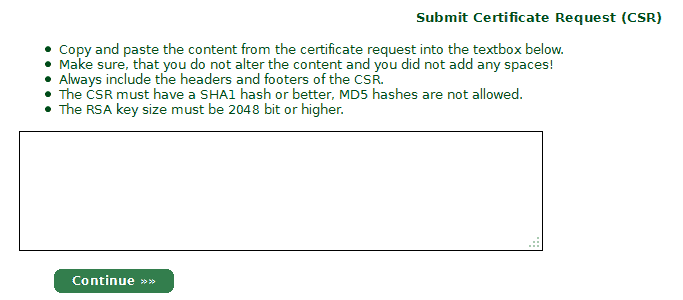
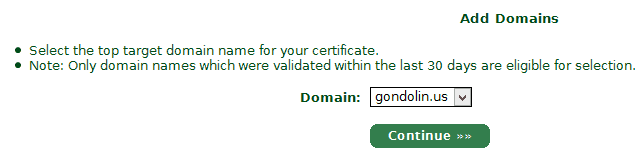
5. Here you select the domain the certificate will fall under, then the subdomain for your certificate (must be the same as your certificate request).
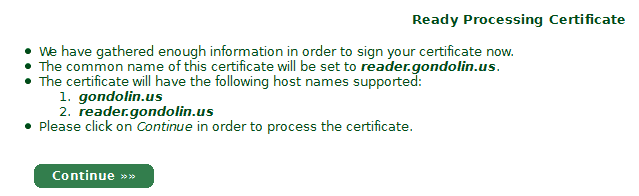
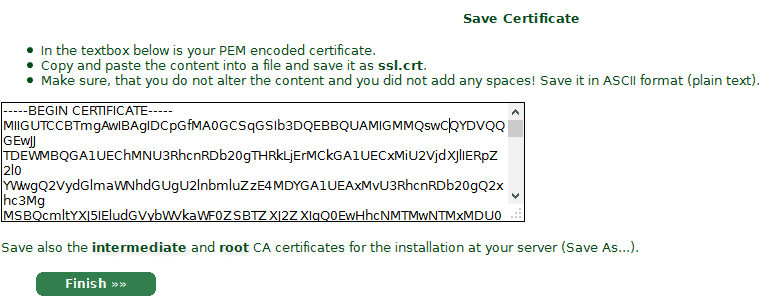
6. StartCom will give you your certificate, paste it into a .crt file. Also BE SURE to download the intermediate and root certs.
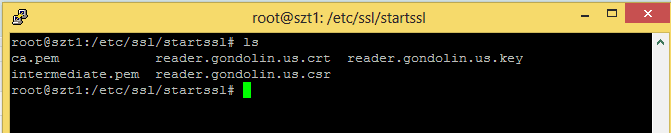
7. Now you have a SSL Certificate (.csr) and Key (.key)
8. Configure Apache2. …this goes below the directory directive in your site config: (e.g. /etc/apache2/sites_available/reader.gondolin.us) be sure to reference your certificate and key as well as StartCom’s root certificate, and chain (this will help out older browers). Note that the certificate can be used for just about any purpose including (IMAP, SMTPS, Mumble server, etc.)
<IfModule mod_ssl.c>
<VirtualHost reader.gondolin.us:443>
ServerAdmin webmaster@localhost
DocumentRoot /var/ttrss/www
<Directory />
Options FollowSymLinks
AllowOverride All
</Directory>
<Directory /var/ttrss/www/>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/
<Directory "/usr/lib/cgi-bin">
AllowOverride None
Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch
Order allow,deny
Allow from all
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log
LogLevel warn
CustomLog ${APACHE_LOG_DIR}/ssl_access.log combined
Alias /doc/ "/usr/share/doc/"
<Directory "/usr/share/doc/">
Options Indexes MultiViews FollowSymLinks
AllowOverride None
Order deny,allow
Deny from all
Allow from 127.0.0.0/255.0.0.0 ::1/128
</Directory>
SSLEngine on
SSLCertificateFile /etc/ssl/startssl/reader.gondolin.us.crt
SSLCertificateKeyFile /etc/ssl/startssl/reader.gondolin.us.key
SSLCertificateChainFile /etc/ssl/startssl/intermediate.pem
SSLCACertificateFile /etc/ssl/startssl/ca.pem
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory /usr/lib/cgi-bin>
SSLOptions +StdEnvVars
</Directory>
BrowserMatch "MSIE [2-6]" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
BrowserMatch "MSIE [17-9]" ssl-unclean-shutdown
</VirtualHost>
</IfModule>