Have you heard about WireGuard?

I was looking at OpenVPN and other VPN options recently and came across WireGuard.
WireGuard is built into the Linux kernel and is now available for just about every platform: Windows, Mac, FreeBSD, Android, iOS. I would just run WireGuard in a VM but if you wanted to it can also run directly on Firewall appliances and devices like EdgeOS, OPNsense, OpenWRT, VyOS, Untangle NG, etc.
What I love about WireGuard is nobody knows it’s there.
It’s like the silent drive on the Red October. It just sits there listening on UDP but doesn’t respond unless it receives the correct public key. So it runs completely stealth and doesn’t show up on a portscan.
Being completely invisible, I believe WireGuard is an excellent option for a VPN. I’d much rather someone not even see an open port where I’m running a VPN, which fits the bill.
WireGuard Features
- Minimal attack surface. It has a small code base, this makes it easier to audit and less likely to have security vulnerabilities
- Deploying is basically the same as SSH with public/private keys
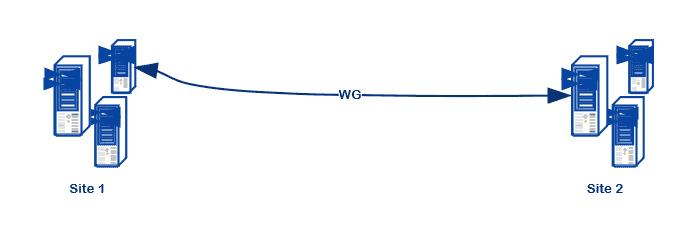
- Supports any network topology (star, site-to-site, mesh, hybrid, etc.)
- Fast. It outperforms every VPN I’ve used. It can basically run at line speed.
- Available on a number of devices, operating systems, appliances, etc.
- Implemented at several large corporations
- Opinionated on cryptography–no downgrade attacks
- Can use a specific DNS server when connected to a VPN
- The client can be configured to route only certain networks through the VPN–or you could tunnel all traffic through it.
- Praised by Linus Torvalds
- Can roam between physical connections (like Mosh) without dropping the tunnel.
There are plenty of guides on setting up WireGuard. Here are a few geared towards some particular configurations.
VPN to LAN (Client/Server)
I set mine up using the traditional client/server VPN model, for now, roughly following this guide.
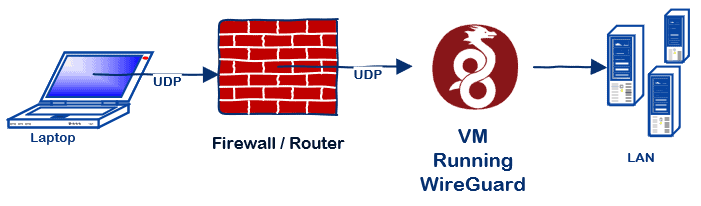
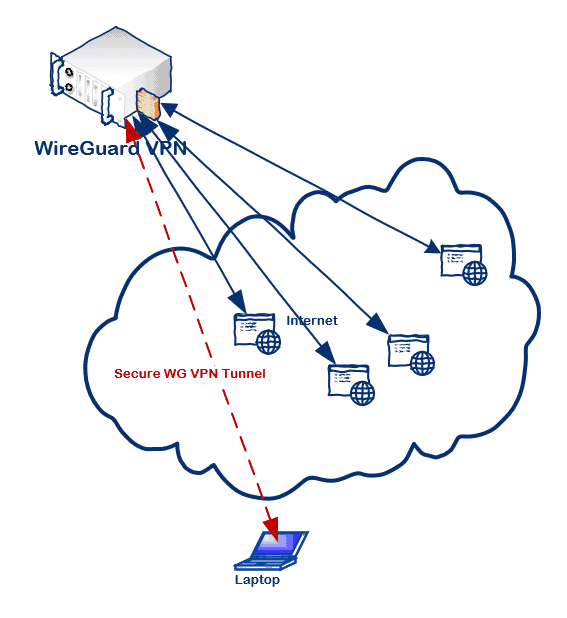
VPN Tunnelling…
You can tunnel all the traffic through the VPN, or just the traffic for a certain network ranges.
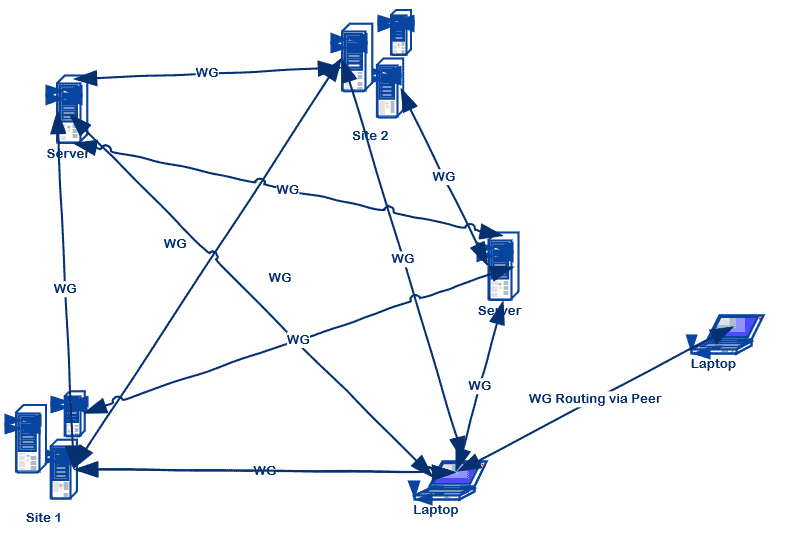
Mesh VPN
Or you can setup a Mesh VPN…, and peers can even route connections through other peers if they’re not directly reachable. This Python package can maintain all the configuration files across any number of nodes.
Other characteristics
WireGuard came out of a rootkit project so it’s not designed to be chatty. When you’re not sending VPN traffic, it’s not sending anything to keep the connection live–unless you need to send packets to get out from behind a NAT. In fact, if you don’t mind it sending out regular keepalive packets, it can initiate UDP hole punching through a NAT with the port closed from outside the Firewall on both sides. Peer to peer directly–no 3rd server needed.
WireGuard is designed to be small and simple, resulting in fewer lines of code than IPSec or OpenVPN, making for a minimal surface attack area.
Oh, and it’s fast. Faster than IPSec, faster than OpenVPN, and faster than every commercial VPN I’ve used. How fast? I don’t know, but it can saturate a gigabit connection easily.
If you’re looking for a VPN, give it a try.