By now, almost everyone has heard of the LastPass breach.

Most cybersecurity professionals are taking a well-reasoned approach that we need to take action but let’s do it right.
Here are my thoughts:
First off, I must compliment LastPass on two things:
- They knew they got hacked.
- They had the integrity to disclose it publicly.
LastPass had tools in place to detect data exfiltration. I suspect several password managers have been hacked without even realizing it.
That said, what did the hackers get?
The hackers got the encrypted vaults and data from fields that were not encrypted. I addressed the unencrypted fields in my LastPass Guide (Appendix A), for reference here is what is not encrypted:
LastPass Data Not Encrypted
- URLs
- Attributes and metadata such as autologin, is it a favorite, item type (database, password, secure note, etc.), when was the last time it was accessed, etc.
- History
- Account Settings
- Account information (your email address, etc.)
What can the hacker do with that unencrypted data?
The worst part of this breach is the unencrypted URL field associated with every vault entry. The data can be used for phishing; additionally, for corporate networks, the attacker probably has a good idea of what technologies are in use and the URLs to get to them. This makes network scanning after intrusion almost not necessary. You can bet nation-states would pay a pretty penny for this information (if it wasn’t a nation-state, to begin with).
What about the encrypted data?
The following data is encrypted with your master password.
- Name
- Folder
- Notes
- Username
- Password
- File Attachments
- Custom Field Data
The main security of LastPass is that that data is encrypted with zero-knowledge to LastPass protected by your master password.
Your Master Password is important. Very important. This password can be used to decrypt all your other passwords and sensitive information stored in LastPass. If your Master Password gets compromised, everything in LastPass gets compromised. – LastPass Guide, Page 14.
You did generate a strong master password, right? At this moment, the hacker is trying to crack those vaults. How long will it take? Well, if you have a short 12-character or easily guessable Master Password it may be cracked already. But if you had a unique, strong master password that’s not guessable, it would take billions of years of computing time to crack it. Hive Systems has a good write-up on password cracking.
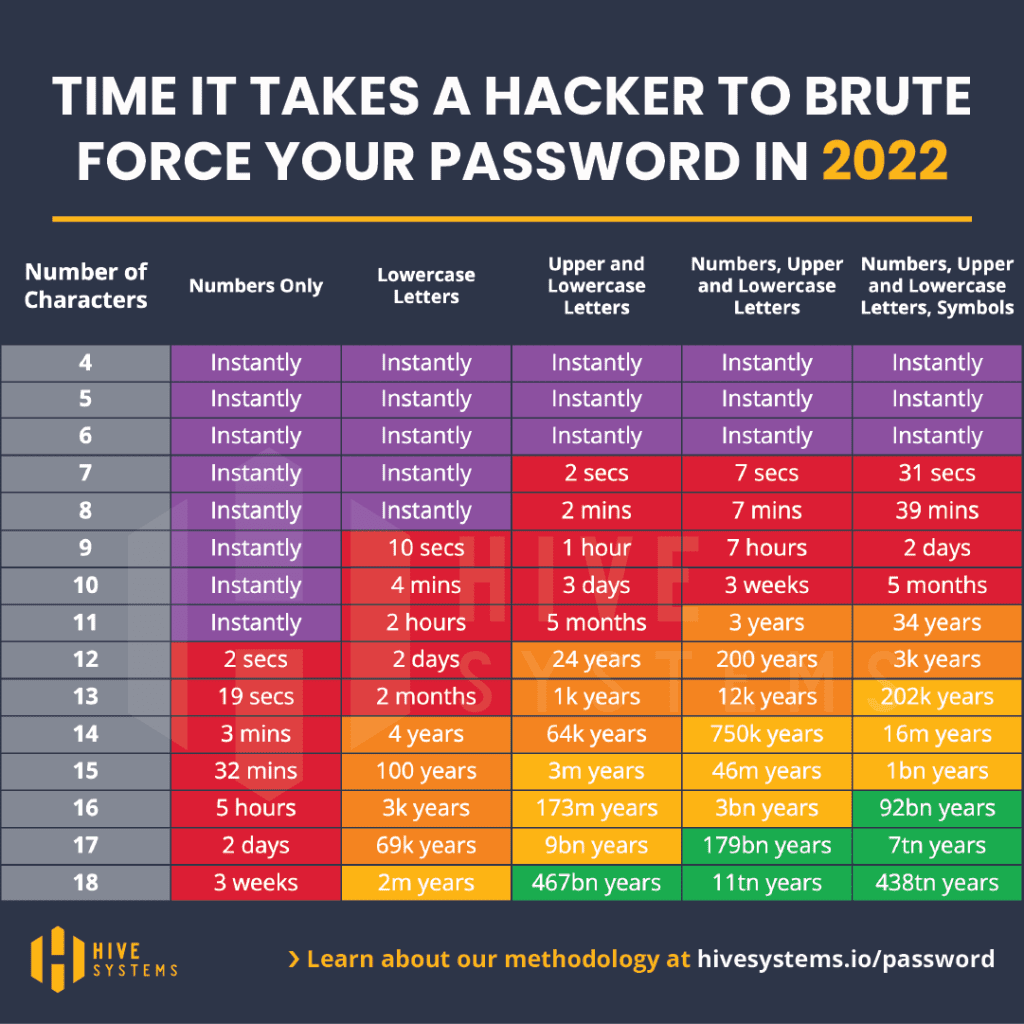
The prudent course of action

Security comes in layers, like a cake. Your layers are going to be things like MFA, access to the vault, your master password, etc. But in this case, the next layer is your vault master password, and if that gets breached, all you have is MFA which probably not all your accounts have. While you may have a robust master password, and it may not be cracked in this lifetime, the likelihood of someone trying to phish your master password has just gone up.
The prudent thing to do is to re-establish multiple security layers. You can do that by changing your Master Password and then all your account passwords. It would also be wise to reset MFA tokens if you’re using the LastPass Authenticator.
Moving away from LastPass
And an additional optional step is moving away from LastPass. One huge reason to move away is that whoever obtained the vaults may start phishing for your LastPass master password credentials. But they will not be successful if you’re simply not using it anymore! While I must reiterate my commendation of LastPass being able to detect the intruder at all, I must criticize them in the following areas:
- They got breached. They had one job… this just shouldn’t have happened to begin with.
- The vault wasn’t entirely zero-knowledge; a lot of and data remains unencrypted (such as URLs). A lot of competitors have actual zero-knowledge vaults that encrypt everything. This would have been an easy security layer for LastPass to implement.
- LastPass has been acquired several times, and it appears to me the new owners are letting it coast. I have seen no real innovation or security improvement from LastPass in the last two years.
- The default number of PBKDF2 iterations (which increases the cracking difficulty) was too small for too long (when I signed up for LastPass the default was 5,000, and I bumped it up to around 200,000). I have heard from other people that the setting was 5,000, 500, and even 1.
- LastPass did not enforce strong passwords. They allowed people to use weak 12-character passwords. Humans still need to bear the responsibility of choosing a weak password–but other password managers enforce stronger passwords.
LastPass Alternatives
- 1Password. 1Password is well regarded and has an extra security benefit in that your vault is encrypted with a secret key in addition to your Master Password. If the 1Password vaults were stolen, this protects vaults even with weak master passwords. Because of the secret key, this looks like the most secure option for people that may use a weak or compromised master password.
- Bitwarden. Bitwarden is an open-source password manager. Open source has an advantage because thousands of eyes have looked at the code. You don’t need to trust Bitwarden to implement security properly because you can look at the code yourself. It even allows you to self-host–you can run your own server. The unofficial Vaultwarden server you can run yourself and gives you most of the benefits of Bitwarden’s paid service for free. For most people, on-prem would be too much of a security risk and effort. You really want to know what you’re doing and have IDS/IPS in front of it, and perhaps place it behind a VPN. But it is still a great option for people running homelabs who want an open-source on-prem option.
- Keeper. Keeper is a more organization / enterprise-type solution, having advanced permissions/roles and the ability to integrate into SIEMs and CI/CD tools. But it also has personal and family plans. It has the most security certifications and audits of password managers, including ISO27001, SOC II, FIPS-140-2, and is StateRAMP and FedRAMP authorized. One weakness is Keeper asks for a recovery question/answer; you’ll want to pick a strong answer (treat it like a second master password, same length and complexity requirements) since the vault is also encrypted with that. For almost every scenario Keeper comes in less expensive than the alternatives.
- KeePass. Finally, if sharing isn’t needed KeePass is an open-source offline password manager. You can still sync the database file across devices using a cloud service such as OneDrive or perhaps SyncThing. One advantage to KeePass is you can encrypt the database using a Yubikey (Amazon) in addition to your master password.
And to reiterate some prudent steps:
- Get a new password manager (optional).
- Reset your master password (and make it a strong one, no less than 20 characters and difficult to guess).
- Reset your account passwords.
- Reset your MFA tokens (if they were stored in LastPass).
They said to him, “Then say Shibboleth,” and he said, “Sibboleth,” for he could not pronounce it right. Then they seized him and slaughtered him at the fords of the Jordan. At that time 42,000 of the Ephraimites fell.
— Judges 12:6 ESV